These days, almost all businesses have concerns about the growing number of cyber threats to network security, web applications, devices, servers, peripherals, and even people and physical buildings. Sometimes shortened to pen test, penetration testing describes an effective method to identify real-world cybersecurity issues before they occur and just as important, how to fix them.
Why penetration of Corporate Networks is essential?
Internal corporate LAN/WAN environments are structured to allow users greater amounts of access with fewer security controls, and this is exactly where the situation becomes exploitable. Any network design flaw or network and server vulnerabilities can result into exploitable areas which is a target of hackers. Multiple surveys indicate that most of the large scale firms and almost all mid-scale firms lack in corporate level cyber security implementations to protect themselves. However it may not be enough with changing times, and hence needs to be periodically tested via a form pen-test to ensure continued cyber security.
How Long Does a Network Penetration Test Take?
The time it takes pen testers to complete their work depends on the organization’s systems’ size and complexity. Testing a one-doctor medical office won’t usually take as long as working with a global enterprise. Of course, the time the test takes may also depend upon any weaknesses or vulnerabilities uncovered and the sensitivity of the information that the security system should protect. With that said, testing projects usually last from one to four weeks. After scoping the project, the testing team can offer a detailed estimate.
FEATURES
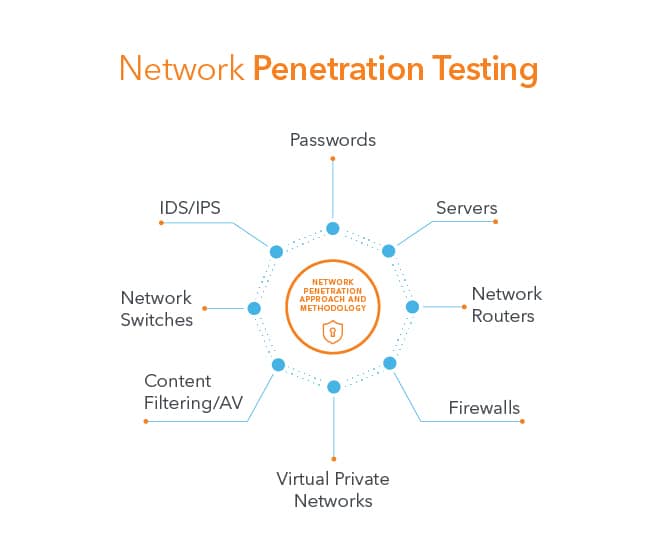
Exploit Categories
- IP network exploits
- Firewall device evasion
- Router device evasion
- Intrusion detection system bypassing
- Perimeter defence exploits
- L2-L3 switch exploits
- VPN Exploits
Standards Followed
- OWASP Top 10 – 2020
- NIST – CWE Standard
Vulnerabilities Detected
- IP ports (TCP / UDP) vulnerabilities
- Device Detection
- Service Mapping
- Service Penetration
- Device misconfiguration exploitation
- Device Penetration
Test Approaches
- Externally over Internet
- Internally from within LAN
